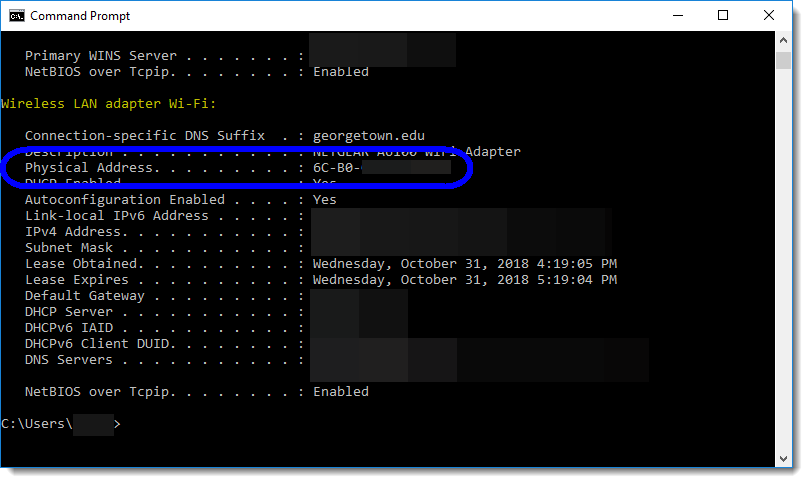
The MAC address is usually based on the hardware. If we both have iPhones and scan the same peripheral, we'll see different UUIDs. IOS generates the UUID on the device and hides the MAC address. Summary - iOS doesn't let you get the MAC address of a device, it gives you a random UUID instead.“.
MAC Randomization. IOS 14 introduced the MAC randomization feature which means that for each SSID, devices running iOS 14 will present a distinct randomized MAC address. This randomized MAC address for each network will not change over time, upon reconnecting to the same SSID, or when the SSID is “forgotten” in the device settings and re-joined later on. I quickly realized that getting directly the MAC address of the device is restricted. Both on iOS and Android you can see that. In iOS 7 and later, if you ask for the MAC address of an iOS device, the system returns the value 02:00:00:00:00:00. If you need to identify the device, use the identifierForVendor property of UIDevice instead.
by Daniele Pantaleone - Sep 21, 2020
On September 16th of 2020, Apple released the latest version of their operating system for mobile devices: iOS 14. This new update, which came out in September like every new iOS release, introduces new restrictions on the network identifiers shared by devices, in order to better protect the privacy of users.
As a consequence of this, devices equipped with the latest version of iOS will hide their MAC address when they connect to a WiFi network, identifying themselves with a randomised address instead. This specifically affects Fing as a constantly changing MAC address equals the identification of devices as “new” on the network even when they are not, as well as an unstable monitoring of the device status.
Previous releases
Starting with the release of iOS 11 in 2017, Apple has begun to introduce restrictions on the availability of network information accessible by third-party apps. The reason why the access to certain information has been restricted is to protect users' privacy, but Apple indirectly affected network monitoring applications available for iOS. This led to the mobilisation of developers and users to save network tools on iOS. Here a list of the main changes Apple has made over the years:
- Starting from iOS 11, the possibility for third-party apps to read the MAC addresses of network connected devices has been removed. These MAC addresses, available in the ARP table of the device, have been changed with a fixed, locally administered MAC address (i.e. 02:00:00:00:00:00) which cannot be used to uniquely identify a device. This limitation has forced all applications that perform network scanning on iOS to adopt a different approach to index network discovered nodes. The lack of MAC addresses also impacts the recognition of the device manufacturer, affecting functionalities to activate and detect devices in the network.
- Starting from iOS 13, third-party applications need the user's consent to access the name (SSID) and identifier (BSSID) of the Access Point to which the device is connected. Since a WiFi network is usually always located in the same geographical area, when a device is connected to a WiFi network, the geographical location of the device can be indirectly inferred, with a certain margin of error. Therefore, Apple has decided to limit access to this information only after the user has granted access to the location. Without access to the location, and therefore without the possibility of obtaining the Access Point identifier, Fing is unable to correctly index and retrieve the scanned networks.
These two limitations have affected all network monitoring apps for iOS, including the iOS version of Fing. The other products made by Fing, namely the Fing version for Android, Fingbox, and Fing Desktop, are not affected by this limitation in any way.
A new limitation with iOS 14: Private MAC Address
Starting from iOS 14 (and similarly from iPadOS 14 and watchOS 7), all devices equipped with the latest version of the Apple mobile/wearable operating system will mask their real MAC address every time they connect to a WiFi network, identifying themselves on the network using a randomised MAC address. The reason behind this further limitation is to be found once again in the protection of user’s privacy by Apple. Quoting Apple:
“To communicate with a WiFi network, a device must identify itself to the network using a unique network address called a media access control (MAC) address. If the device always uses the same WiFi MAC address across all networks, network providers and other network observers can more easily relate that address to the device's network activity and location over time. This allows a kind of user tracking or profiling, and it applies to all devices on all WiFi networks.
To reduce this privacy risk, iOS 14, iPadOS 14 and watchOS 7 use a different MAC address for each WiFi network. This unique, static MAC address is your device's private WiFi address for that network only.”
This new feature is somewhat similar to the one Google introduced with the release of Android 10, but imposes stronger restrictions that we will describe below:
How this impacts Fing
As is evident from the table above, the introduction of Private MAC Addresses in Apple iOS 14, iPadOS 14 and watchOS 7 systems does not allow the use of the MAC address as a stable identifier of a network device, and this affects all Fing products as the restriction relates to published network information and not to what can be retrieved from an iOS device. Due to this limitation, all network monitoring applications that use the MAC address as an identifier for devices on the network will consider a device as a “new” network device:
- Fingbox, Fing Desktop and Fing for Android will notify the device as new whenever the device's MAC address changes.
- The impact will also have repercussions on Fingbox's Digital Presence, which is closely linked to the presence on the network of a “personal” device. Since the device will be identified as “new” every now and then, the tracking of the “old” device will be automatically lost because Fingbox will no longer detect the status change (even if in reality the device is always the same).
- This new restriction, on the other hand, will not cause any problems for the iOS version of Fing, because since the release of iOS 11, IP addresses are used to index devices connected to a network, and therefore the introduction of MAC addresses randomisation does not impact the app in any way.
How this impacts Fing Device Recognition
Although the Fing device identification works at best with non-private MAC addresses, the recognition engine and AI algorithms have been evolving to cope with local addresses, as iOS, Android and Windows started to partly hide the MAC’s since 2017. When Fing Device Recognition can make use of network protocols like DHCP, HTTP user agent and hostname, it is able to leverage them in order to recognise the device and classify its type, brand and model.
How to mitigate the side effects
The Private MAC Addresses can be disabled from the device, for each WiFi network. Therefore, to improve the recognition of new devices and continue to monitor changes in status, we recommend to disable the use of Private MAC Addresses for your network on your own iOS devices. Here how to proceed:
iPhone, iPad or iPod touch
- Open the iOS Settings app, then tap WiFi.
- Tap the information button next to a network.
- Disable Private Address using the appropriate Switch.
Apple Watch
- Open the Settings app, then tap WiFi.
- Tap the name of the network you joined. If you haven't joined the network yet, swipe left on its name and tap more.
3. Disable Private Address using the appropriate Switch.
Ios For Mac Download
Because Private MAC Addresses are bound to the access point identifier rather than the WiFi network name, if you have multiple access points serving your network in WiFi roaming, you may be required to perform this operation multiple times for each device. Indeed, a new randomised MAC address will be generated every time the iOS device jumps from being connected to a WiFi access point A to another WiFi access point B of your network.
Sources
This article is for network administrators and other people who manage their own network. If you're trying to join a Wi-Fi network, one of these articles should help:
- Mac: Connect to Wi-Fi and resolve Wi-Fi issues.
- iPhone, iPad or iPod touch: Connect to Wi-Fi and resolve Wi-Fi issues.
Before changing the settings on your router
- Back up your router's settings, just in case you need to restore the settings again later.
- Update the software on your devices. This is critical for ensuring your devices have the latest security updates and work the best they can with each other.
- First, install the latest firmware updates for your router.
- Then, update the software on your other devices, such as on your Mac and on your iPhone or iPad.
- On each device that had previously joined the network, you may need to forget the network to ensure the device uses the router's new settings when rejoining the network.
Router settings
To ensure that your devices can reliably reconnect to your network, apply these settings consistently to each Wi-Fi router and access point, and to each band of a dual-band, tri-band or other multi-band router.
Network name (SSID)
A single, unique name (case sensitive)
The Wi-Fi network name, or service set identifier (SSID), is the name your network uses to advertise its presence to other devices. It's also the name that nearby users will see on their device's list of available networks.
Use a name that's unique to your network, and make sure all routers on your network use the same name for every band they support. For example, don't use common names or default names, such as linksys, netgear, dlink, wireless or 2wire, and don't give your 2.4 GHz and 5 GHz bands different names.
If you don't follow this guidance, your devices may not connect reliably to your network, to all of the routers on your network or to all of the available bands of your routers. And devices that join your network are more likely to encounter other networks that have the same name, and then automatically try to connect to them.
Hidden network
Disabled
Mac Address For Ios Devices
A router can be configured to hide its network name, or SSID. Your router may incorrectly use 'closed' to mean hidden, and 'broadcast' to mean not hidden.
Hiding the network name doesn't conceal the network from being detected or secure it against unauthorised access. And because of the way devices search for and connect to Wi-Fi networks, using a hidden network may expose information that can be used to identify you and the hidden networks you use, such as your home network. When connected to a hidden network, your device may display a privacy warning due to this privacy risk.
To secure access to your network, use the appropriate security setting instead.
Security
WPA3 Personal for better security, or WPA2/WPA3 Transitional for compatibility with older devices
The security setting defines the type of authentication and encryption used by your router, and the level of privacy protection for data transmitted over its network. Whichever level of security you choose, always set a strong password to join the network.
- WPA3 Personal is the newest, most secure protocol currently available for Wi-Fi devices. It works with all devices that support Wi-Fi 6 (802.11ax), and some older devices too.
- WPA2/WPA3 Transitional is a mixed mode that uses WPA3 Personal with devices that support that protocol, while allowing older devices to use WPA2 Personal (AES) instead.
- WPA2 Personal (AES) is appropriate when you can't use one of the more secure modes. In that case, also choose AES as the encryption or cipher type, if available.
Settings that turn off security, such as None, Open or Unsecured, are strongly discouraged. Turning off security disables authentication and encryption and allows anyone to join your network, access its shared resources (including printers, computers and smart devices), use your Internet connection, and monitor data transmitted over your network or Internet connection (including the websites you visit). This is a risk even if security has been turned off temporarily or for a guest network.
Don't create or join networks that use older, deprecated security protocols such as WPA/WPA2 Mixed Mode, WPA Personal, TKIP, Dynamic WEP (WEP with 802.1X), WEP Transitional Security Network, WEP Open or WEP Shared. These are no longer secure, and they reduce network reliability and performance. Apple devices display a security warning when joining such networks.
MAC address filtering, authentication and access control
Disabled
When this feature is enabled, your router can be set up to only allow devices that have specified media access control (MAC) addresses to join the network. Reasons why you shouldn't rely on this feature to prevent unauthorised access to your network:

- It doesn't prevent network observers from monitoring or intercepting traffic on the network.
- MAC addresses can easily be copied, spoofed (impersonated) or changed.
- To help protect user privacy, some Apple devices use a different MAC address for each Wi-Fi network.
To secure access to your network, use the appropriate security setting instead.
Automatic firmware updates
Enabled
If possible, set your router to install software and firmware updates automatically as they become available. Firmware updates can affect the security settings available to you, and they deliver other important improvements to the stability, performance and security of your router.
Radio mode
All (preferred),or Wi-Fi 2 through Wi-Fi 6 (802.11a/g/n/ac/ax)
These settings, available separately for the 2.4 GHz and 5 GHz bands, control which versions of the Wi-Fi standard the router uses for wireless communication. Newer versions offer better performance and can support more devices concurrently.
Flash For Ios Mac
It's usually best to enable every mode that's offered by your router, rather than a subset of these modes. All devices, including older devices, can then connect using the fastest radio mode they support. This also helps reduce interference from nearby legacy networks and devices.
Bands
Enable all bands that are supported by your router
A Wi-Fi band is like a road that data can flow down. More bands provide more data capacity and performance for your network.
Channel
Auto
Each band of your router is divided into multiple, independent communication channels, like different lanes on a road. When channel selection is set to automatic, your router will select the best Wi-Fi channel for you.
If your router doesn't support automatic channel selection, choose whichever channel performs best in your network environment. That varies depending on the Wi-Fi interference in your network environment, which can include interference from any other routers and devices that are using the same channel. If you have multiple routers, configure each one to use a different channel, especially if they are close to each other.
Channel width
20 MHz for the 2.4 GHz band
Auto orall widths (20 MHz, 40 MHz and 80 MHz) for the 5 GHz band
Channel width specifies the size of 'pipe' available to transfer data. Wider channels are faster but more susceptible to interference, and also more likely to interfere with other devices.
- 20 MHz for the 2.4 GHz band helps to avoid performance and reliability issues, especially near other Wi-Fi networks and 2.4 GHz devices, including Bluetooth devices.
- Auto or all channel widths for the 5 GHz band ensures the best performance and compatibility with all devices. Wireless interference is less of a concern in the 5 GHz band.
DHCP
Enabled, if your router is the only DHCP server on the network
Dynamic host configuration protocol (DHCP) assigns IP addresses to devices on your network. Each IP address identifies a device on the network and enables it to communicate with other devices on the network and Internet. A network device needs an IP address, much like a phone needs a phone number.
Your network should only have one DHCP server. If DHCP is enabled on more than one device (such as on both your cable modem and router), address conflicts may prevent some devices from connecting to the Internet or using network resources.
DHCP lease time
8 hours for home or office networks; 1 hour for hotspots or guest networks
DHCP lease time is the length of time that an IP address assigned to a device is reserved for that device.
Wi-Fi routers usually have a limited number of IP addresses they can assign to devices on the network. If that number is depleted, the router can't assign IP addresses to new devices, and these devices can't communicate with other devices on the network and Internet. Reducing DHCP lease time allows the router to reclaim and reassign old IP addresses that are no longer being used faster.
NAT
Enabled, if your router is the only device providing NAT on the network
Network address translation (NAT) translates between addresses on the Internet and addresses on your network. NAT can be understood by imagining a company's post room, where deliveries to employees at the company's address are directed to employee offices within the building.
You should generally only enable NAT on your router. If NAT is enabled on more than one device (such as on both your cable modem and router), the resulting ”double NAT” may cause devices to lose access to certain resources on the network or Internet.
WMM
Enabled
WMM (Wi-Fi multimedia) prioritises network traffic to improve the performance of a variety of network applications, such as video and voice. All routers that support Wi-Fi 4 (802.11n) or later should have WMM enabled by default. Disabling WMM can affect the performance and reliability of devices on the network.
Device features that can affect Wi-Fi connections
These features may affect how you set up your router or the devices that connect to it.
Private Wi-Fi Address
If you're connecting to a Wi-Fi network from an iPhone, iPad, iPod touch or Apple Watch, find out more about using private Wi-Fi addresses in iOS 14, iPadOS 14 and watchOS 7.
Location Services
Make sure your device has Location Services turned on for Wi-Fi networking, because regulations in each country or region define the Wi-Fi channels and wireless signal strength allowed there. Location Services helps to ensure your device can reliably see and connect to nearby devices, and that it performs well when using Wi-Fi or features that rely on Wi-Fi, such as AirPlay or AirDrop.
On your Mac:
- Choose Apple menu > System Preferences, then click Security & Privacy.
- Click the lock in the corner of the window, then enter your administrator password.
- In the Privacy tab, select Location Services, then select Enable Location Services.
- Scroll to the bottom of the list of apps and services, then click the Details button next to System Services.
- Select Wi-Fi Networking, then click Done.
On your iPhone, iPad or iPod touch:
- Go to Settings > Privacy > Location Services.
- Turn on Location Services.
- Scroll to the bottom of the list, then tap System Services.
- Turn on Networking & Wireless (or Wi-Fi Networking).
Auto-Join when used with wireless carrier Wi-Fi networks
Wireless carrier Wi-Fi networks are public networks set up by your wireless carrier and their partners. Your iPhone or other Apple mobile device treats them as known networks and connects to them automatically.
If you see a ”Privacy Warning” under the name of your carrier's network in Wi-Fi settings, your mobile identity could be exposed if your device were to join a malicious hotspot impersonating your carrier's Wi-Fi network. To avoid this possibility, you can prevent your iPhone or iPad from automatically rejoining your carrier's Wi-Fi network:
- Go to Settings > Wi-Fi.
- Tap next to the wireless carrier's network.
- Turn off Auto-Join.